How Long Does NIS2 Implementation Take and Why You Should Start Now
You probably know the feeling – everyone in the company has their own priorities. Operations, customers, deliveries, finance. Somewhere between all that and the IT department, cybersecurity should also have its place. Right now, we're facing more cyberattacks than ever before. At the same time, the world and business move at lightning speed, and there are always too many priorities. If you sense that preparing for NIS2 won't become a priority anytime soon, at least take a few minutes to read about what the consequences could be.
Waiting to start preparing for new regulations could be the most expensive mistake your company makes. Implementing security measures in line with NIS2 doesn’t happen overnight. It requires a plan, resources, and above all – time, which is already ticking.
NIS2 implementation is not a matter of days
Based on our experience, companies typically achieve compliance with NIS2 requirements within 6 to 12 months. However, this depends on the size of the organization, the current level of security management, and the technical infrastructure. For larger or more complex businesses, the implementation may take significantly longer.
The entire process begins with mapping the initial state – without this, a proper GAP analysis cannot be conducted. This so-called gap analysis reveals the areas that need attention during implementation. In addition to rolling out technical security measures, it's essential to ensure proper documentation of all processes and have clearly recorded company assets, risks, suppliers, employee training history, and much more.
Now, let’s be honest – how many of these steps could your team realistically complete in just three months?
Who waits today, will struggle to find people tomorrow
It’s important to note that there is a serious shortage of skilled and experienced cybersecurity professionals on the market. If your internal resources are limited, you may quickly run into trouble. A CISO (Chief Information Security Officer) who understands both business and the specific demands of NIS2 is a rare find today. The later a company starts, the smaller its chances of securing the expertise it needs.
This is exactly why Whirr Crew offers CISO oursourcing. Through this model, companies gain access to a senior-level cybersecurity manager who can define a security strategy, oversee the security management system, and prepare the company for audits — without the need to expand the internal team.
You Can’t Do It Without a System. We Rely on the PDCA Cycle
Cybersecurity success isn’t about “having some documents in the cloud.” It’s about knowing what you’re doing, why you’re doing it, and proving that it works. In many organizations, implementing NIS2 will require new processes, assigned responsibilities, and proper employee training. There’s a lot to be done—and time won’t wait.
At Whirr Crew, we follow the proven Plan – Do – Check – Act (PDCA) approach to managing cybersecurity effectively:
Plan: Define your goals and priorities, and build a realistic roadmap.
Do: Implement the required measures and train your people.
Check: Continuously monitor and evaluate the effectiveness of your actions.
Act: Make improvements and respond to emerging threats.
Cybersecurity isn’t a one-time project. It’s a system of processes that must become part of your company’s day-to-day operations. That’s the only way to ensure long-term, effective protection from ever-evolving risks.
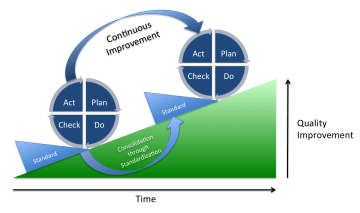
Depiction of the PDCA cycle (also known as the Deming cycle). Continuous quality improvement is achieved by iteratively moving through the cycle and reinforcing progress through standardization. | Johannes Vietze
What obligations are coming into effect now?
The new cybersecurity legislation in the Czech Republic (Act No. 264/2025 Coll.) comes into force on 1 November 2025.
From this date, the first legal deadlines begin to apply – and they are not just about “changes to implement later,” but about immediate responsibilities. Below are the key steps that should already be a priority this autumn.
1. Within 60 days of the legislation taking effect – notification of regulated service
Organizations providing a regulated service must notify the National Cyber and Information Security Agency (NÚKIB). Upon receiving this notification, the organization is automatically registered as a service provider.
2. Within 30 days of registration – reporting contact details
Once the organization receives the decision on registration, it must submit the contact details of responsible persons within 30 days (e.g. cybersecurity manager, CISO, incident response contact).
3. Within 1 year of registration – implementation of measures and incident reporting
A one-year transitional period begins after registration, during which organizations must:
implement security measures in line with NIS2 requirements and national legislation,
establish a process for reporting security incidents,
complete internal documentation (risk analysis, security policies, staff training records, asset inventory, etc.).
After this deadline, the organization must be fully compliant with the new cybersecurity law and prepared for potential audits.
Time to Get Started
NIS2 is not just another bureaucratic obligation. It is an opportunity to finally set up cybersecurity in a way that makes real sense — from a business, operational, and strategic perspective. And those who start now won’t just meet their legal obligations next year — they’ll also sleep better at night.
Schedule a consultation with Whirr Crew.
We’ll help you create a realistic plan to secure your business.